How MixMode Detects Ransomware, Exploits and Other Techniques Used by Hacktivists Against Critical Infrastructure

When a power station falters, a water system is infiltrated, or a hospital network goes dark the real world impact is no longer theoretical. Critical infrastructure (CI) runs on complex, interconnected systems where small anomalies can hide adversary activity that can quickly become large-scale disruptions. Today, these CI sectors face mounting risks from the unconventional and unpredictable nature of hacktivists, ranging from sole individuals leveraging bot swarms services to organized syndicates and/or state actors.
Sitting at the intersection of cyber threats and protest, hacktivists use hacking as a tool for activism, not money or state power. Individuals or loosely organized groups use hacking techniques to promote a political, social, ideological, or moral cause. Their activities are driven by activism.
Recent analyses show attackers increasingly targeting Industrial Control Systems (ICS), Operational Technology (OT), and AI-driven workflows, exploiting exposed interfaces, unpatched vulnerabilities, and novel tactics to cause operational disruption, data extortion, and physical safety hazards.
MixMode provides a unified, AI-first cybersecurity platform that delivers real-time, pre-emptive threat detection and prevention. By ingesting and analyzing high-fidelity network traffic at line speed alongside log repositories, MixMode applies patented Third Wave AI to dynamically learn organizational behavior and identify deviations indicative of compromise—all within a single, streamlined solution.
This dual approach—combining raw communication streams with correlated log data—ensures full visibility from node to edge, painting a complete picture of the environment through observable actions.
No separate tools.
No manual log forwarding.
No complex integrations.
Just powerful, network-centric visibility fused with log intelligence for predictive threat prediction from day one.
The Foundation: Comprehensive Visibility Through Communication and Log Correlation
MixMode begins with deep, passive network traffic analysis that captures rich metadata, protocol details, connection patterns, and behavioral context at line speed. This source of truth, revealing host-to-host communications, protocol anomalies, and subtle changes that traditional logs or endpoint data alone cannot provide.
To achieve holistic coverage, MixMode also ingests and correlates data from log repositories, such as SIEM systems, CloudTrail, VPC Flow Logs, or other event sources such as direct event feeds. This integration allows for cross-referencing raw network communications with logged observable actions—user behaviors, system events, and audit trails—providing end-to-end visibility from individual nodes (devices, endpoints) to the network edge (perimeters, cloud boundaries).
The platform deploys lightweight sensors to collect network-derived intelligence while seamlessly pulling in log data, enabling patented self-supervised AI to baseline the entire environment without relying on rules, historical datasets, or GPU infrastructure.
This correlated approach achieves extremely low false positives (97%+ reduction) and dramatically lower alert volume (93% fewer alerts), while surfacing prioritized, context-rich insights across enterprise IT, OT, cloud, and air-gapped segments.
Detecting Hacktivists and Ransomware in Real Time
Hacktivists—often motivated by geopolitical conflicts—conduct persistent campaigns against CI, scanning for exposed HMIs, SCADA systems, VNC interfaces, and weak authentication points. Ransomware operators, meanwhile, pursue financial gain through double extortion, recurring attacks, and evolving models like Extortion-as-a-Service.
MixMode identifies both categories early and effectively by analyzing correlated network and log data:
- Reconnaissance & Initial Access: Detects unusual port scanning, brute-force attempts on exposed industrial interfaces, connections from temporary or suspicious infrastructure, and anomalous geographic patterns typical of hacktivist operations, cross-checked against log entries for authentication attempts.
- Lateral Movement & Exploitation: Spots unexpected east-west traffic spikes, protocol misuse, credential abuse, and exploit attempts (e.g., session hijacking or known vulnerability chains) before attackers pivot deeper into OT environments, enriched by log correlations for user and system actions.
- Ransomware Behaviors: Recognizes pre-encryption indicators such as unusual file access patterns, mass modifications, command-and-control communications, and outbound data staging—even in previously unseen variants—verified through log audits of file system changes.
- AI Workflow Threats: Identifies anomalies tied to enterprise AI systems, including unusual API calls, poisoned data feeds, or network manifestations of prompt-injection attacks, aligned with logged API interactions.
Because the AI operates directly on fused network and log context, MixMode shifts defenders from reactive mean-time-to-detect to proactive mean-time-to-prevent.Key Indicators of Risk and Exploitations—Surfaced Natively
MixMode prioritizes and contextualizes these common indicators through its integrated AI analysis of correlated data sources:
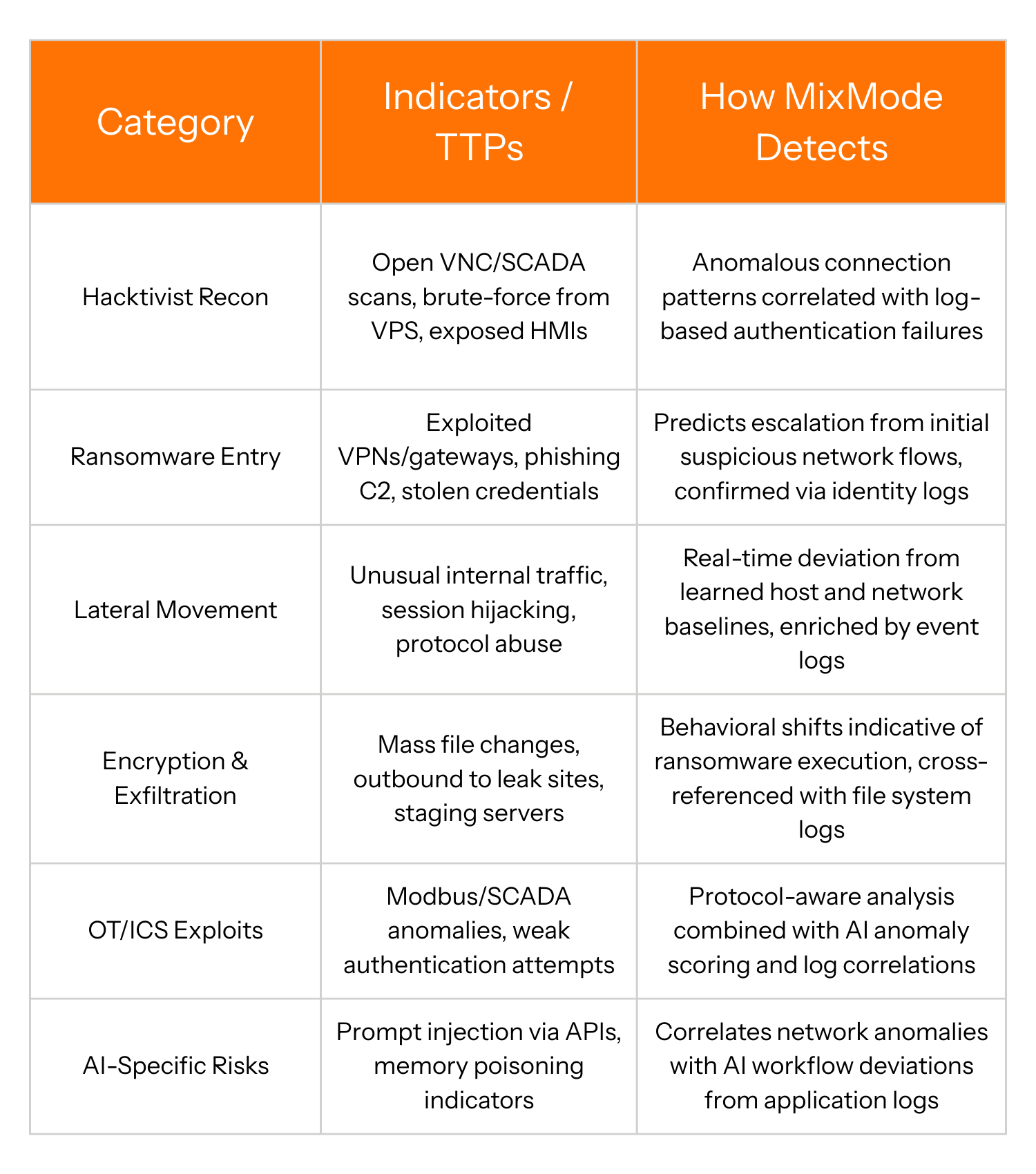
These detections draw from real-world trends and CISA guidance, delivered as actionable, low-noise alerts rather than raw data dumps.
Advantages of the MixMode Platform
- Single-Pane Simplicity: All network visibility, log correlation, AI analysis, alerting, and investigation happen in one platform—no stitching together separate tools.
- Rapid Deployment & Immediate Value: Often live in under an hour, learning baselines instantly and surfacing previously missed threats on day one.
- OT & Air-Gapped Support: Full visibility into industrial protocols and segmented environments without compromising security posture.
- Cost & Operational Efficiency: No GPU dependency, lower infrastructure footprint, and consolidation that extends rather than replaces existing investments like SIEMs.
- Compliance Alignment: Supports NERC CIP, zero-trust architectures, and regulatory requirements in critical sectors.
Proactive Protection in One Platform
MixMode transforms network traffic and log data into predictive intelligence, enabling organizations to stay ahead of hacktivist campaigns, ransomware campaigns, and sophisticated exploit chains targeting critical infrastructure. By combining deep network context at line speed with correlated log repositories in a single solution, it delivers the visibility, speed, and accuracy needed in an era of geopolitically motivated and financially driven cyber threats—ensuring a full, actionable picture of the environment through every observable action.
As attacks grow more creative and persistent, a unified, AI-powered approach is no longer optional, it’s essential. Explore MixMode to experience how real-time network intelligence fused with log correlation can safeguard your operations. Schedule a demo today and see the difference proactive, low-noise detection makes.
The environment already reveals the threats.
MixMode correlates it all intelligently.


